In a staggering revelation, cybersecurity experts have uncovered a colossal cache of over 26 billion exposed records online, branding it as the “mother of all breaches.” Contrary to conventional breaches, this massive dataset doesn’t stem from a solitary security incident but rather represents an amalgamation of multiple breaches, often orchestrated by data enrichment entities. The process of data enrichment involves amalgamating first-party data from internal sources with diverse data from external or internal systems, transforming it into a valuable asset for organizations due to its increased utility and insights.
Although the researchers identified a staggering 26 billion records, the possibility of duplicates is high. What sets this data apart is its sensitivity, making it a goldmine for malicious actors beyond just credential information.
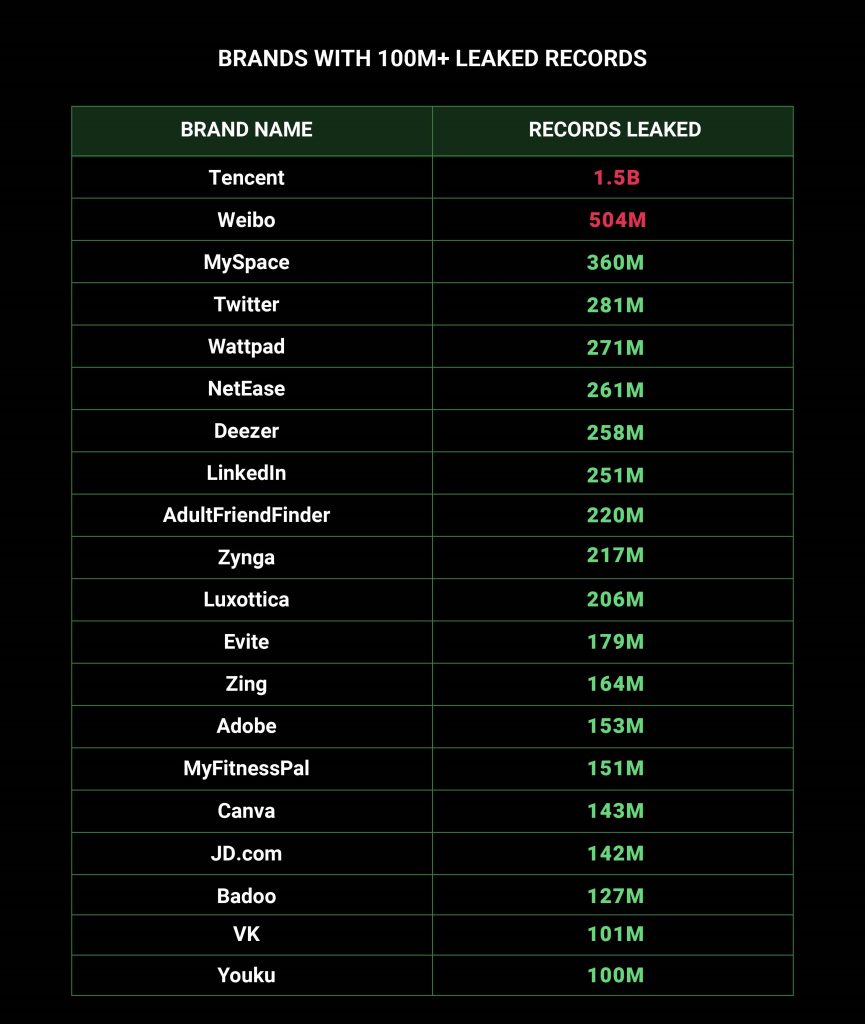
In a parallel development concerning leaked personal data, a cybercriminal self-identifying as “emo” asserts possession of 15 million unique records of Trello accounts from a project management tool, raising significant concerns given Trello’s widespread usage across various organizations.
While Atlassian, the company overseeing Trello, denies any breach, suspicions linger as the alleged breach appears to be an exploitation of a vast collection of email addresses tested against Trello rather than a direct intrusion.
This revelation prompts a critical question: when does a substantial leak of personal information qualify as a breach? A pragmatic definition suggests that a breach occurs when data is unintentionally exposed in a vulnerable system due to insufficient access controls or security vulnerabilities in the software.
Some argue that a true breach only results from hacking, relegating other forms of data exposure as leaks. Applying this perspective, neither dataset can be conclusively categorized as originating from a breach, as one was stumbled upon, while the other was generated using a legitimate API, albeit in larger quantities than intended.
However, for those impacted, the distinction between a breach, scraping, or data enrichment is inconsequential; their personal information is now vulnerable to exploitation by cybercriminals.
To ascertain whether personal data is exposed online, individuals can utilize a free Digital Footprint scan by entering their email address for a comprehensive report. The findings may reveal surprising insights, emphasizing the importance of understanding the exposure status and potential risks associated with leaked information.
The report may unveil instances of breaches, including the exposure of passwords. If recognizable passwords surface, it is advisable to change them promptly, implement two-factor authentication, and assess whether the passwords have been reused across multiple accounts.
Given scammers’ adeptness at leveraging breached information for social engineering attacks, individuals are urged to remain vigilant. Even the mere knowledge of data being leaked in a breach can become a focal point for phishing attacks, underscoring the need for proactive security measures.
The previous year witnessed an alarming surge, with over 2,000 companies and government entities reporting data breaches affecting more than 400 million personal accounts. Establishing identity monitoring is recommended to receive timely alerts whenever personal data surfaces in a new breach, reinforcing the need for heightened cybersecurity measures in an era of escalating digital threats.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


