The notorious ransomware collective, ALPHV, also known as BlackCat, is innovating its extortion methods with the introduction of an API for their leak site. This enhancement is aimed at increasing the exposure of their cyber-attacks, in an attempt to mount additional pressure on their victims to pay ransoms.
The move comes in the wake of ALPHV’s recent breach of beauty giant, Estée Lauder, where the company dismissed any engagement with the threat actor’s efforts to negotiate a ransom payment.
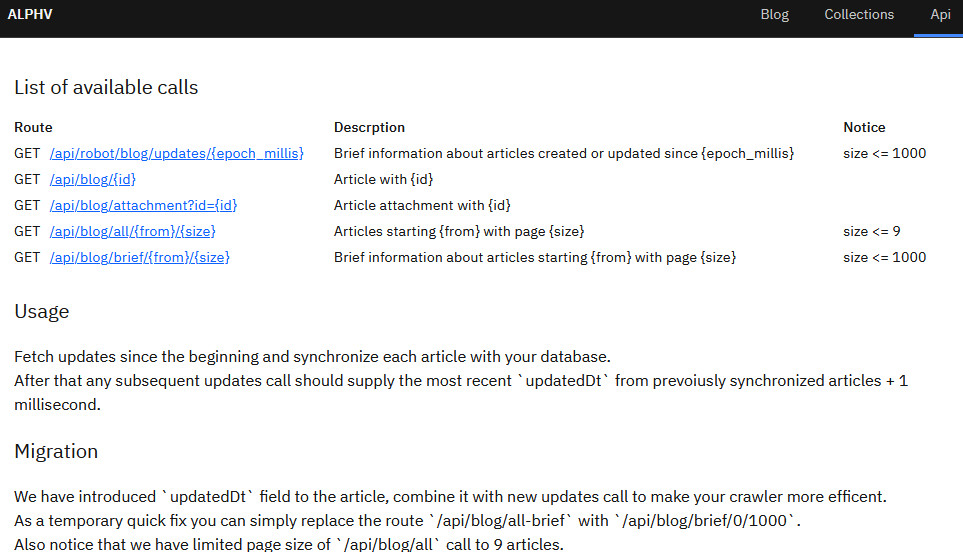
API calls and Python crawler under scrutiny
Prominent researchers have recently discovered a new page with instructions for utilizing the API on the ALPHV/BlackCat data leak site. The purpose is to receive real-time updates about new victims.
APIs, short for Application Programming Interfaces, are typically used to establish communication between two software components, conforming to predefined protocols and definitions.
Cybersecurity research group, VX-Underground, was among the first to spot the new section on ALPHV’s site. However, the “feature” has been partially accessible for a few months, albeit not for the wider audience.
The cybercriminal group released the API calls, assisting in acquiring various information about new victims added to their leak site or updates from a specific date. They also provided a Python-based crawler to facilitate the retrieval of the latest information on the data leak site.
Ransomware Victims: A Declining Trend
Although ALPHV did not provide any specific reason behind the release of the API, industry insiders speculate it could be due to the decrease in victims succumbing to ransomware demands.
Coveware, a ransomware incident response firm, notes that the proportion of victims that suffered a ransomware attack and paid a ransom “declined to an all-time low of 34%” in this year’s second quarter.
However, this does not mean that all ransomware gangs are suffering. Some are still raking in large sums by focusing their efforts on the supply chain to impact a greater number of organizations. For instance, the Clop ransomware group has reportedly made at least $75 million from their extensive MOVEit data theft campaign, potentially impacting hundreds of companies.
In a show of defiance, Estée Lauder did not respond to any communications from ALPHV, firmly indicating that it would not negotiate with the attackers over the stolen files.
This reaction enraged the ALPHV group, leading to a sarcastic message mocking the company’s security measures. The message indicated that the security experts hired in the aftermath of the breach were unsuccessful, as the network was still compromised.
With the decline in ransom payment, ransomware groups are now compelled to devise innovative strategies to exert pressure and secure their desired funds. The practice of making leaked data easily accessible to a wider audience appears to be the latest pressure tactic from ransomware gangs. However, many cybersecurity experts believe such efforts are likely to prove futile in the long run.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


