A recent discovery by security researchers has unveiled a new variant of the notorious Qilin ransomware, specifically designed to target VMware ESXi servers. This Linux encryptor, considered one of the most sophisticated seen to date, demonstrates the adaptability of cybercriminals in the face of the enterprise’s growing reliance on virtual machines.
As businesses increasingly opt for virtual machines to optimize resource utilization, ransomware groups have adapted, creating specialized encryptors for VMware ESXi servers. Unlike many ransomware strains that leverage existing code, Qilin stands out by crafting its own encryptors, focusing on Linux servers.
Security researcher MalwareHunterTeam recently unearthed a Linux ELF64 encryptor used by the Qilin ransomware gang. Shared with BleepingComputer for analysis, this encryptor not only targets Linux and FreeBSD servers but places a significant emphasis on VMware ESXi servers. Particularly, it concentrates on encrypting virtual machines and deleting associated snapshots, making it a unique and potent threat.
Qilin’s encryptor boasts an embedded configuration specifying details such as file extensions for encryption, processes to terminate, files to encrypt or exclude, and folders to encrypt or exclude. What sets it apart is the extensive customization it offers through numerous command-line arguments. These options include enabling debug mode, conducting dry runs without actual encryption, and tailoring the encryption of virtual machines and their snapshots.
In a detailed analysis, We highlighted the default configuration of Qilin’s encryptor, revealing exclusions and targeting criteria. The ransomware avoids specific processes, directories, and files, while actively targeting others for encryption. Notably, Qilin’s encryptor is capable of sparing certain virtual machines from encryption.
Upon execution, the ransomware detects the underlying server type (Linux, FreeBSD, or VMware ESXi) and adapts its behavior accordingly. For VMware ESXi servers, Qilin employs esxcli and esxcfg-advcfg commands not previously observed in other ESXi-targeting encryptors. VMware expert Melissa Palmer suggested these commands may have been copied from VMware support bulletins to address known bugs and enhance performance.
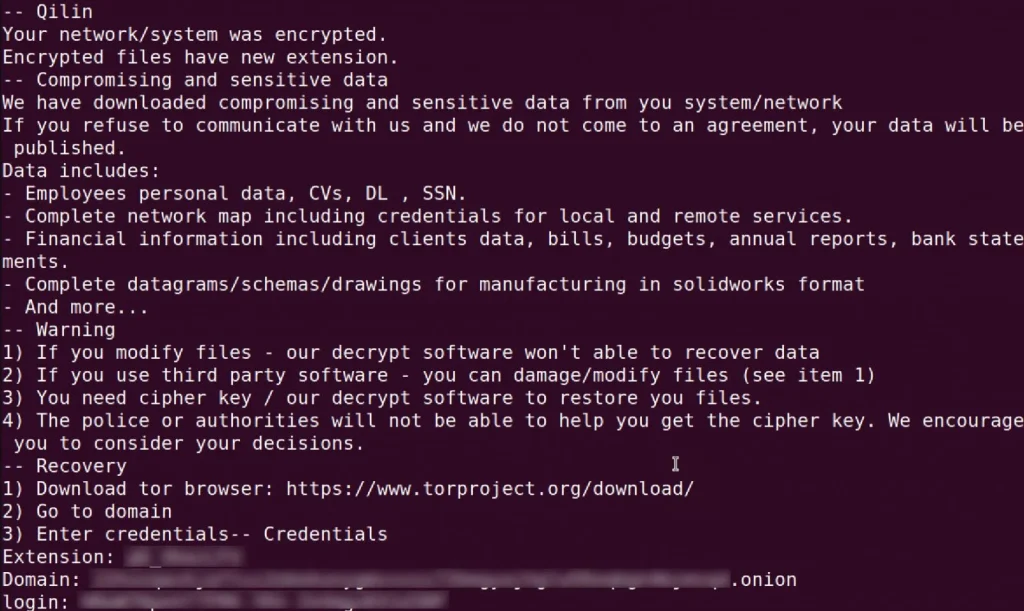
Before encrypting identified virtual machines, Qilin terminates all running VMs and deletes their snapshots. The ransomware then encrypts the targeted files, appending the configured extension to their names. Each folder affected hosts a ransom note, [extension]_RECOVER.txt, containing links to the gang’s Tor negotiation site and login credentials for victim communication.
BleepingComputer reports ransom demands associated with Qilin ranging from $25,000 to multimillion-dollar figures. The Qilin ransomware operation, formerly known as “Agenda,” rebranded in September 2022 and has since been actively targeting enterprises. Operating with a double-extortion strategy, the threat actors breach networks, exfiltrate data, and then deploy the ransomware, leveraging both the stolen data and encrypted files to coerce victims into paying the ransom.
The most recent attack attributed to Qilin targeted Yanfeng, a prominent auto-parts giant, signaling the continued and heightened activity of this evolving ransomware operation in late 2023.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


