In a startling revelation, cybercriminals have successfully exploited a critical zero-day vulnerability, identified as CVE-2023-20198, to compromise and infiltrate more than 10,000 Cisco IOS XE devices with malicious implants. The affected devices span across various products running Cisco IOS XE software, including enterprise switches, aggregation and industrial routers, access points, wireless controllers, and more.
Leading threat intelligence firm VulnCheck discovered that the vulnerability was extensively exploited in attacks specifically targeting Cisco IOS XE systems equipped with the Web User Interface (Web UI) feature, alongside enabled HTTP or HTTPS Server features. The company conducted scans on internet-facing Cisco IOS XE web interfaces, revealing thousands of compromised hosts. VulnCheck has even released a specialized scanner designed to identify these implants on affected devices.
Jacob Baines, CTO of VulnCheck, expressed serious concerns, stating, “Cisco buried the lede by not mentioning thousands of internet-facing IOS XE systems have been implanted. This is a bad situation, as privileged access on the IOS XE likely allows attackers to monitor network traffic, pivot into protected networks, and perform any number of man-in-the-middle attacks.”
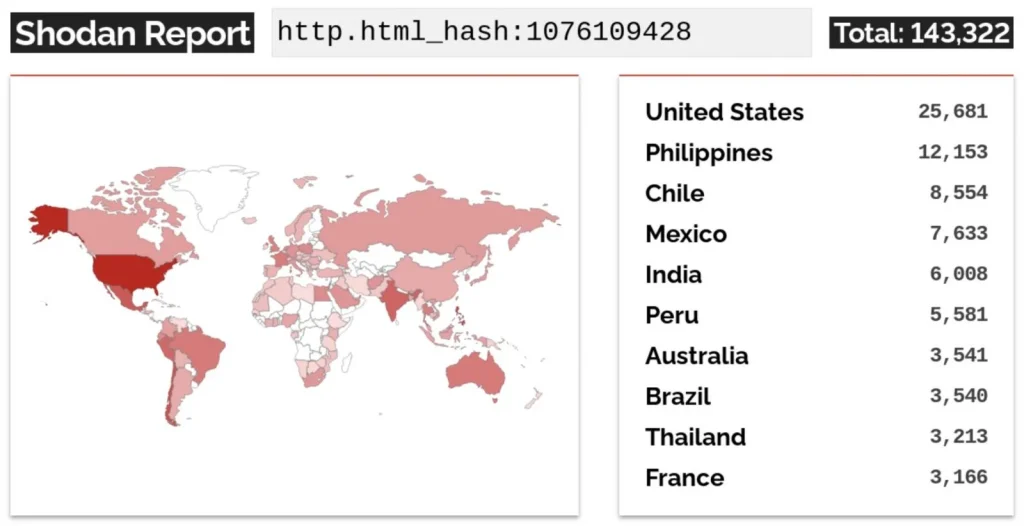
VulnCheck has, so far, identified approximately 10,000 implanted systems through fingerprinting. However, this number is expected to rise as their investigation unfolds. A search on Shodan, shared by Aves Netsec CEO Simo Kohonen, currently reveals over 140,000 Internet-exposed devices with Cisco’s Web UI enabled.
Cisco has urged administrators to implement mitigation measures promptly. They revealed that unauthenticated attackers can exploit the IOS XE zero-day to gain full administrator privileges, enabling them to remotely take complete control over compromised Cisco routers and switches. Cisco strongly advised disabling the vulnerable HTTP server feature on all internet-facing systems until an official patch is released.
The company detected the CVE-2023-20198 attacks in late September after reports of unusual behavior on a customer device were received by Cisco’s Technical Assistance Center (TAC). Evidence suggests that the attackers initiated their activities on September 18, creating local user accounts named “cisco_tac_admin” and “cisco_support.” The attackers deployed malicious implants using CVE-2021-1435 exploits and other undisclosed methods, granting them the ability to execute arbitrary commands at the system or IOS levels on compromised devices.
Cisco suspects that these clusters of activities were orchestrated by the same threat actor. The first cluster possibly served as the actor’s initial attempt and testing their code, while the October activity indicated an expansion of their operation, establishing persistent access through the deployment of the implant.
The company has issued a stern recommendation for administrators to remain vigilant and scrutinize suspicious or recently created user accounts, as these might indicate malicious activity associated with this threat. This incident follows a prior warning from Cisco in September, urging customers to patch another zero-day vulnerability (CVE-2023-20109) in its IOS and IOS XE software, which had also been targeted by attackers in the wild.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


