A recent alert from the FBI has shed light on an alarming rise in ransomware campaigns that deploy multiple malware variants on a victim’s network, leading to system encryption in less than two days.
This latest Private Industry Notification issued by the FBI was instigated by patterns observed since July 2023.
The authoritative agency highlighted the deployment of two unique ransomware strains by cybercriminals during their attack on various organizations. The notable variants used in these swift assaults include Diamond, Hive, LockBit, Karakurt, Royal, Quantum, and AvosLocker.
According to the FBI, “Dual ransomware deployment has led to a mix of data breaches, extraction, and significant financial implications due to ransoms.”
The bureau emphasized the potential severity of facing a second ransomware attack after an initial compromise.
Previously, there was typically a span of at least 10 days between successive ransomware attacks on the same target. In stark contrast, the majority of such incidents now occur within 48 hours of one another, as the FBI’s statistics reveal.
BleepingComputer’s conversation with Bill Siegel, CEO & Co-Founder of Coveware, revealed that double-encryption has persisted for some time. He stated, “Some cyber attackers deliberately deploy two separate strains for every attack. We often witness simultaneous attacks using MedusaLocker and Globemposter by a single criminal entity.”
Moreover, Siegel commented on situations where two unique ransomware factions access a network after its initial breach, both executing attacks in close succession.
A concerning observation shared by the FBI detailed how, from early 2022, several ransomware groups have started tweaking their data theft utilities, malware, and wipers to avoid detection.
In certain scenarios, malevolent software with data-erasure capabilities was set to stay inactive on infiltrated systems. This software activates at set intervals, annihilating data across compromised networks.
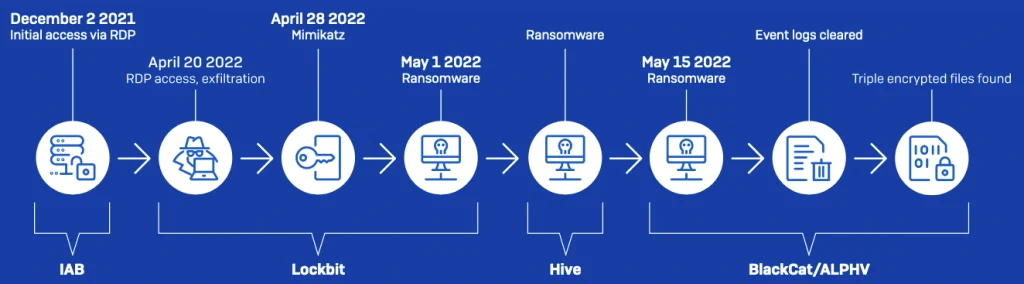
Sophos X-Ops incident response teams reported a disturbing incident from last year. An automotive manufacturer faced breaches from three different factions: LockBit, Hive, and ALPHV/BlackCat, within a short span of two months.
Sophos disclosed that some files were encrypted multiple times. They noted, “As the Hive attack began a mere 2 hours post the Lockbit assault, both attacks were in progress, leading to repeated encryption of certain files.”
For countering such ransomware threats, the FBI emphasizes building strong ties with their regional FBI Field Offices. They also recommend routine system updates and comprehensive network scans for any latent vulnerabilities.
Moreover, it’s crucial to safeguard remote access tools like RDP, VNC, etc., with access granted strictly through VPNs and fortified with robust passwords and mandatory multi-factor authentication.
The bureau also advises segmenting networks, ensuring critical servers are contained within VLANs to amplify security. Consistent scans and network audits remain vital for pinpointing devices susceptible due to missing updates.


