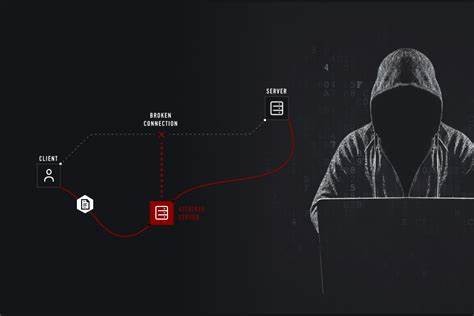
Researchers from the University of South Australia and Charles Sturt University have unveiled a groundbreaking algorithm designed to identify and intercept man-in-the-middle (MitM) attacks on unmanned military robots.
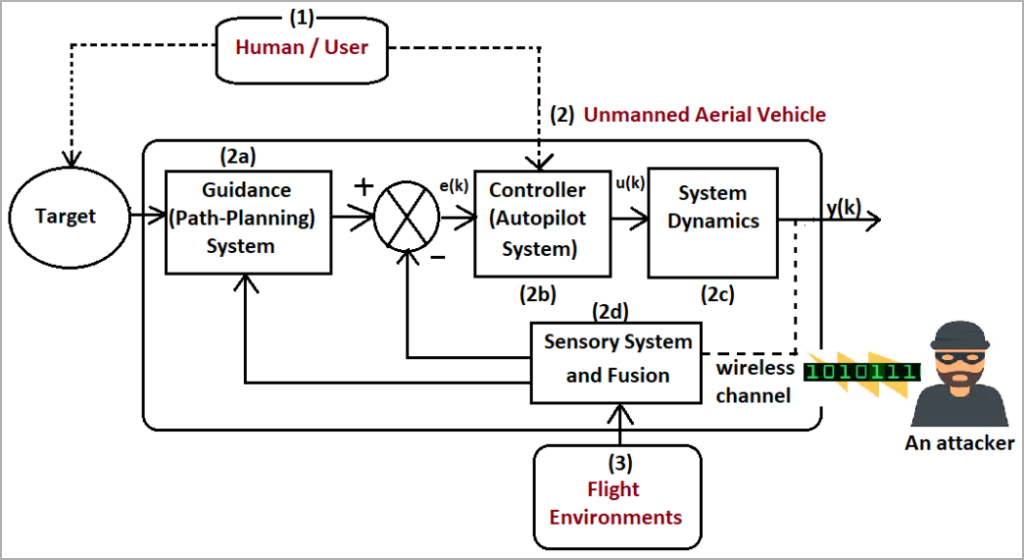
MitM attacks, which involve intercepting data traffic between two parties, pose a significant threat to unmanned military vehicles by enabling malicious actors to eavesdrop, inject false data, or even assume control of the robots. Professor Anthony Finn, an expert involved in the study, emphasized the vulnerability of the robot operating system (ROS) due to its extensive networking, especially in the era of Industry 4.0.
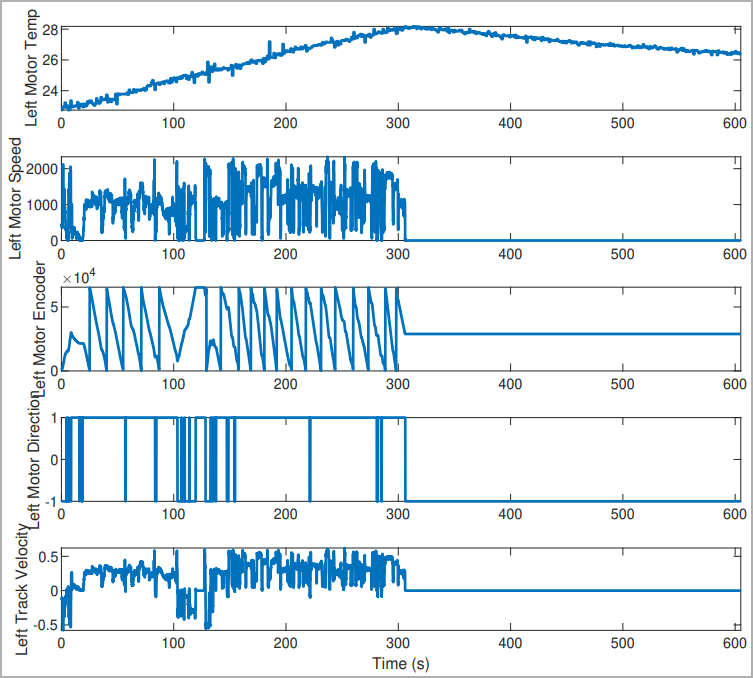
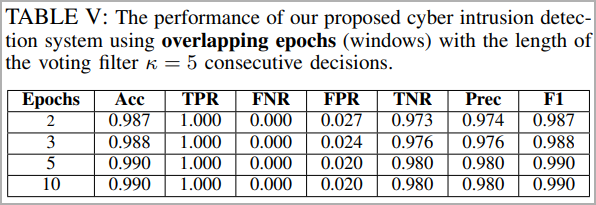
To counter these threats, the researchers harnessed machine learning techniques to develop an innovative algorithm capable of swiftly detecting and neutralizing MitM attempts. The algorithm was rigorously tested on a replica of the U.S. Army’s GVR-BOT (TARDEC), successfully preventing attacks in 99% of cases while minimizing false positives to less than 2%.
Detecting MitM attacks in crewless vehicles and robots is notoriously complex due to their fault-tolerant operating modes. The researchers devised a sophisticated system that analyzes the robot’s network traffic data using node-based methods, packet data scrutiny, and flow-statistic-based analysis of metadata from packet headers.
The team’s technical paper outlines the development of a deep learning convolutional neural network (CNN) model with multiple layers and filters, ensuring robust cyberattack detection. Real tests on the replica bot, simulating various cyber-attacks, demonstrated exceptional accuracy even after minimal training epochs, showcasing the algorithm’s efficiency.
Moreover, the researchers expressed their interest in exploring the algorithm’s effectiveness across diverse robotic platforms, including unmanned aerial vehicles, with their faster and more intricate dynamics. This cutting-edge intrusion detection system promises enhanced security not only for ground robots but also for advanced applications in the realm of unmanned aircraft and beyond.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.